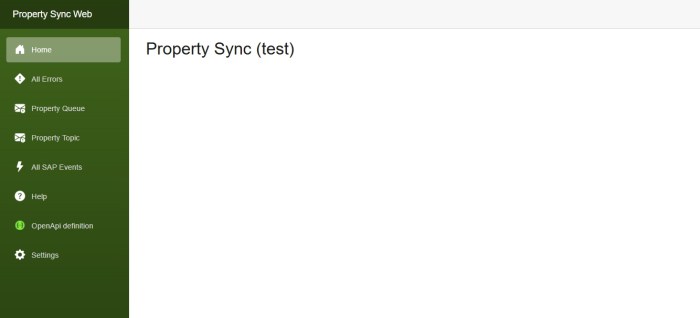
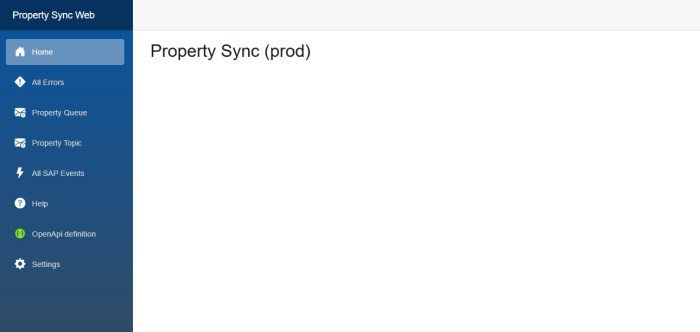
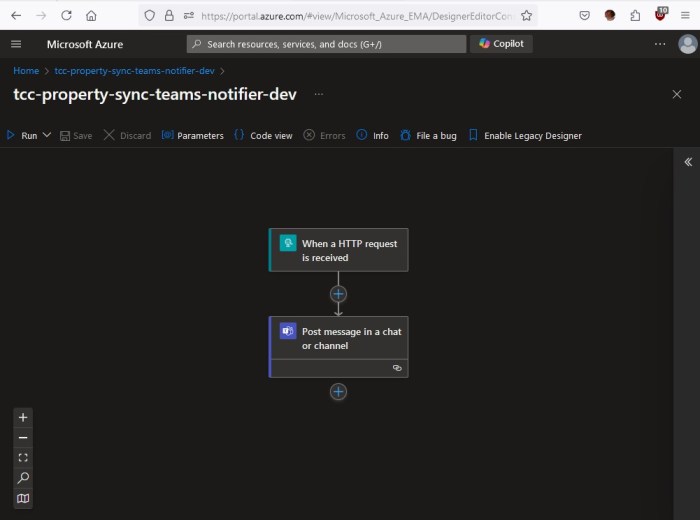
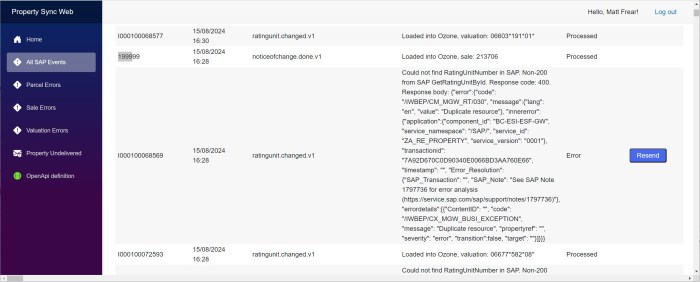
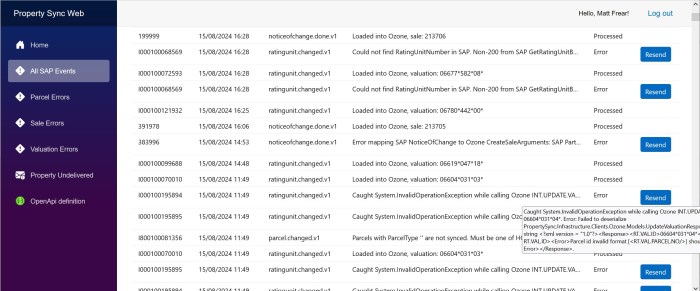
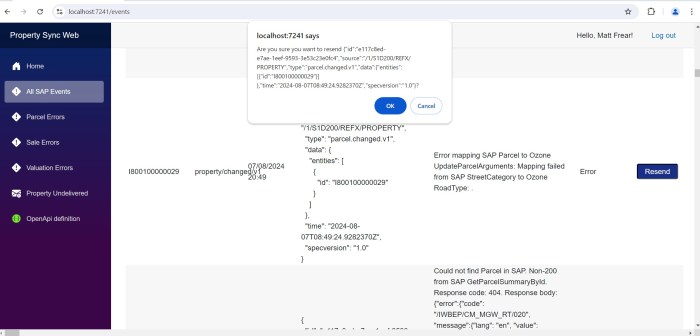
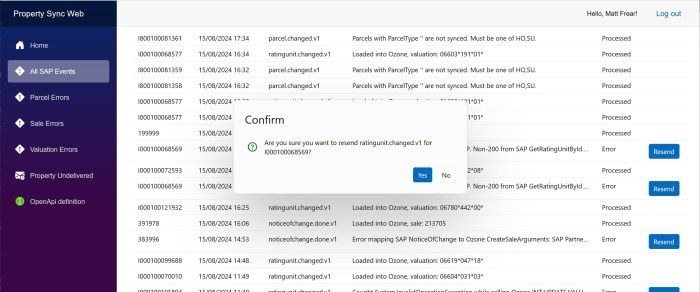
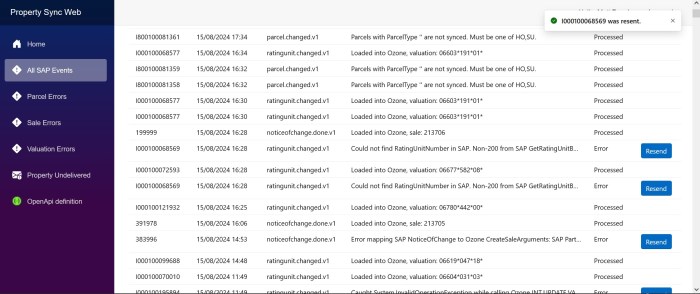
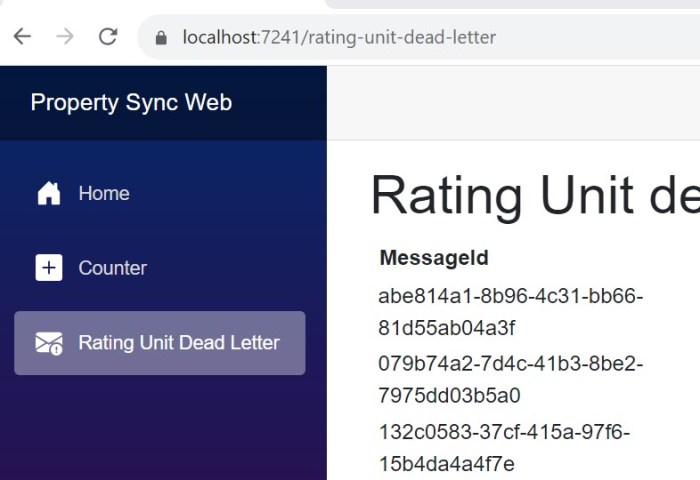
Our client wanted to have a slightly different color scheme for our internal application for each environment, i.e. dev, test and production.
I implemented this by injecting an IConfiguration which I wrote about in 2024.
The component we need to change is in MainLayout.razor, the div with class=”sidebar”.
I’m not sure how to change the css via code, or if it’s possible, so I used an inline style to the div.
MainLayout.razor:
@inherits LayoutComponentBase
@inject IConfiguration Configuration
<div class="page">
<div class="sidebar" style="background-image: linear-gradient(180deg, @SidebarTopColor 0%, @SidebarBottomColor 70%);">
<NavMenu />
</div>
<FluentDialogProvider />
<FluentTooltipProvider />
<FluentMessageBarProvider />
@code {
private string SidebarTopColor = "#052767"; // dark sapphire blue - these are the Blazor default colors
private string SidebarBottomColor = "#3a0647"; // dark purple
protected override void OnInitialized()
{
var environment = Configuration["Environment"]?.ToLowerInvariant() ?? "local";
switch (environment)
{
case "dev":
SidebarTopColor = "#b4b369"; // yellowy greeny
SidebarBottomColor = "#545432"; // dark olive green
break;
case "test":
SidebarTopColor = "#40651b"; // greenish
SidebarBottomColor = "#294211"; // dark green
break;
case "prod":
SidebarTopColor = "#0854A0"; // victoria blue
SidebarBottomColor = "#354a5f"; // dark blue grey
break;
}
}
}